5 causes that make your company more vulnerable to a cyberattack
Any company can be the victim of a cyberattack. However, there are five main causes that make companies even more vulnerable, leaving the door wide open to be attacked very easily. Do you identify any of them in your company?
According to Microsoft’s Data Security Index, 83% of organizations have suffered more than one data breach in their history. This makes it clear that cybercriminals are constantly looking for vulnerabilities in enterprise systems and launching attack attempts, usually successfully.
They just need a lucky day.
And companies, even knowing the risk they run, become easy targets because many do not invest enough in cybersecurity to protect their business assets and anticipate cybercriminals.
Many think it won’t happen to them or that it won’t be as serious and catastrophic as they usually tell… Or, worse, that, in case of an attack, they have it under control.
Until they are attacked.
It is at that precise moment that they remember cybersecurity.
In this article, we look at the top five causes that make companies easy targets for cybercriminals and how to address each of them to reduce risk.
Not keeping abreast of new cyber-attacks and their sophistication.
Technologies such as artificial intelligence have enabled attackers to design more sophisticated strategies, making threat detection more difficult. Methods such as ransomware attacks, which lock systems until a ransom is received, or Deepfakes, attacks that use AI to fake voices or videos, are becoming everyday problems for companies.
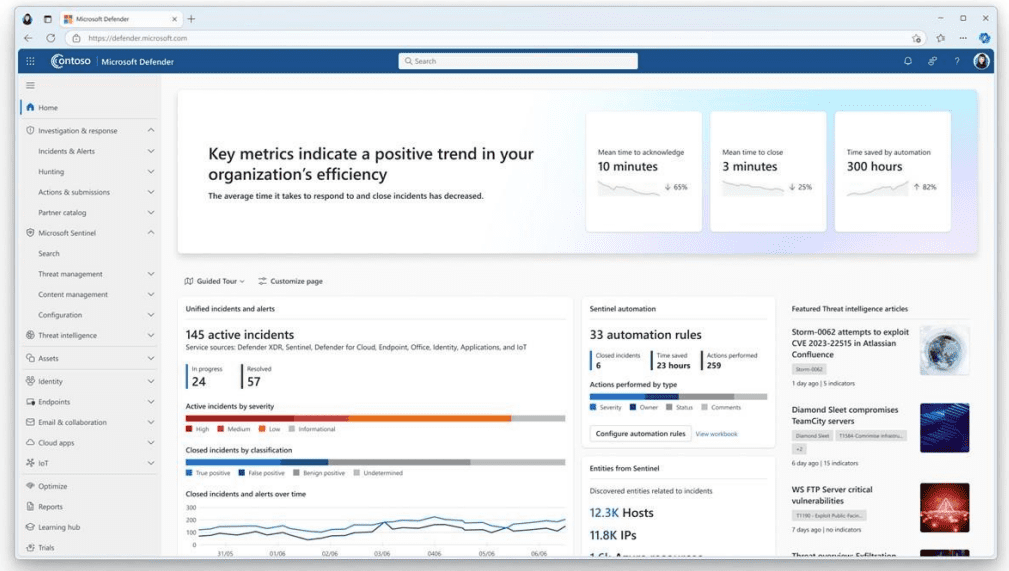
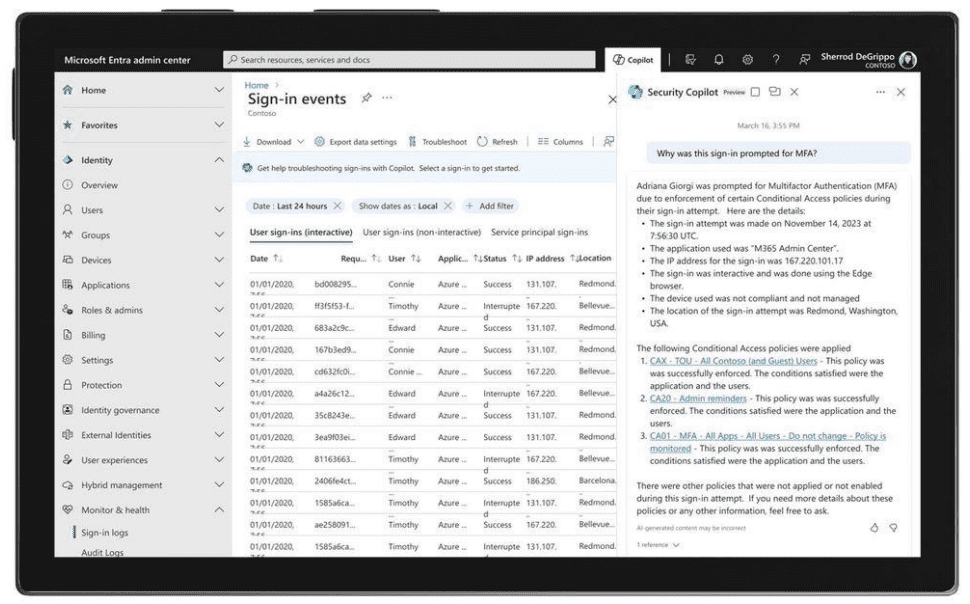
To address these threats, it is essential to have advanced systems in place to monitor and block attacks before they cause damage. Security technologies such as Microsoft’s, which analyze more than 78 trillion signals daily, enable companies to stay abreast of the latest attack trends.
Lack of awareness in the Management Committee.
A common misconception is that cybersecurity is solely the responsibility of the IT team. However, the strategic decisions made by business leaders directly influence the security posture of the enterprise.
When senior management does not prioritize cybersecurity, the investments needed to protect corporate assets are often put on the back burner.
To change this paradigm, leaders must understand that cybersecurity is a fundamental pillar of business continuity. Performing regular risk audits and actively participating in the definition of security policies are key steps to achieve a complete defense.
3. Poor employee training
A malicious email, a suspicious link or a weak password can be enough to compromise a company’s entire network. Employees, without proper training, are often the weakest link in the security chain. In fact, phishing attacks remain one of the main cyber-attacks.
That is why it is essential to invest in continuous employee training. Initiatives such as attack simulations and awareness campaigns help to create an organizational culture that is more resilient to cyber threats.
4. Not having a comprehensive cybersecurity strategy.
Many companies rely on ad hoc or disconnected solutions, leading to gaps in their protection. Without a comprehensive strategy, it is difficult to prevent, detect and respond to cyberattacks.
An effective solution involves implementing a strategy that combines advanced integrated tools and a strategic plan that includes processes, policies and continuous expert oversight.
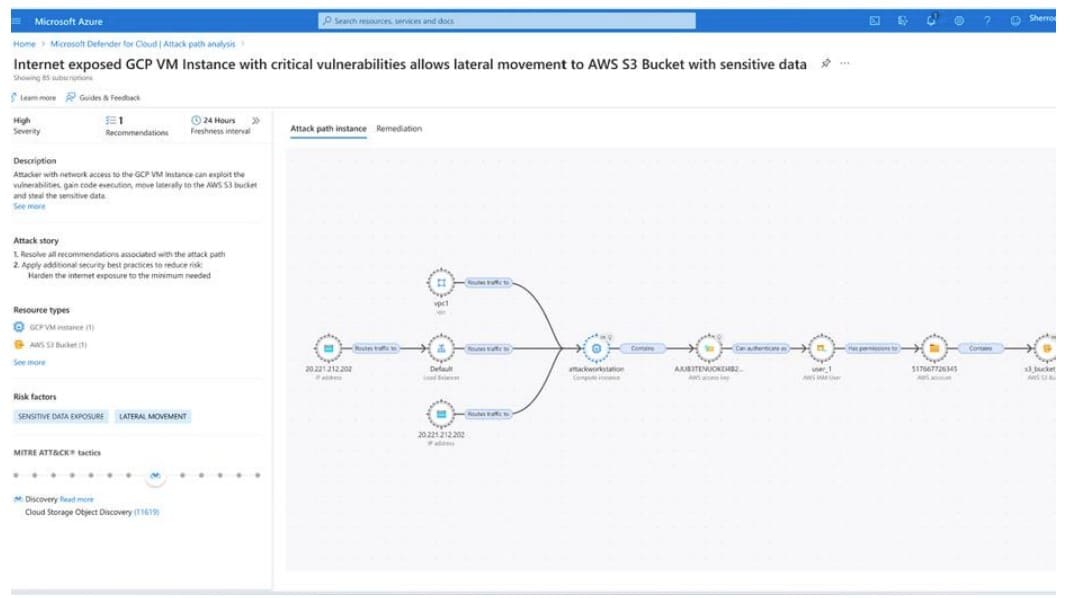
For example, many companies choose a cybersecurity SOC for comprehensive protection, managing everything from early detection to automated incident response, combined with the support of a specialist who is up to date with all the latest developments and solutions.
Which brings us to the last point…
5. Not having the right specialists to manage cybersecurity.
Cybersecurity is not just a technology issue; it requires expertise and specialized skills. Without trained personnel, companies are at a disadvantage.
In these cases, outsourcing cybersecurity management to a specialized partner can make all the difference. Working with cybersecurity experts allows companies to benefit from proactive solutions, regular audits and constant monitoring, ensuring that they are always one step ahead of attackers.
How to reduce the chances of suffering a cyber attack
The companies most vulnerable to cyberattacks have one thing in common: they underestimate the importance of a sound cybersecurity strategy and delay taking action until it is too late.
If you are a business leader, prioritize training, strengthen your systems and seek support from cybersecurity experts to ensure your company is prepared to face increasingly dangerous cybersecurity challenges.
A cybersecurity strategy with cloud solutions, combined with advanced tools, is the only way to ensure cyber resilience.
In Softeng we have designed a service SOC / CSIRT, intelligent and proactive, combining Microsoft technology along with advanced security solutions themselves, to obtain and maximize a global defense against new threats.